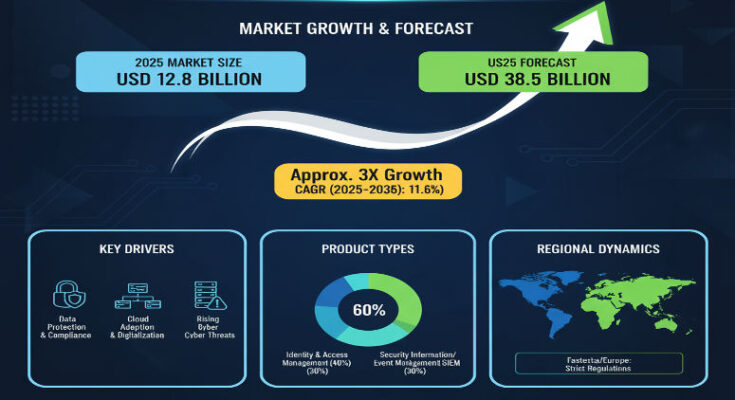
As cloud computing, hybrid environments, and hyperscale data centers proliferate around the world, the value of logical security—identity control, access management, encryption, threat detection—has escalated dramatically. In 2025, the global Data Center Logical Security Market is estimated at USD 12.8 billion, and it is projected to climb to USD 38.5 billion by 2035, growing at a compound annual growth rate (CAGR) of approximately 11.6%. What this reflects is not just expanding demand, but increasing sophistication in how organizations safeguard critical data and infrastructure.
Key Drivers & What’s Fueling Growth
Several interlocking trends are pushing growth upward:
-
Increasing cyber-attacks targeting data center assets are making logical security not optional, but foundational. Threat vectors, including insider threats, phishing, zero-day vulnerabilities, and ransomware, are pressuring operators to invest heavily in detection, response, and prevention tools.
-
Regulatory and compliance demands are rising globally. Data centers are under pressure from governments and industry bodies to meet strict standards for data protection, privacy, breach reporting, and secure access.
-
Cloud adoption, and hybrid models in particular, are expanding the footprints data centers must secure. As more workloads and data move outside of traditional boundaries, logical security architectures that can work across on-premises, cloud, and edge environments are becoming essential.
-
The rise of zero-trust security models and AI/ML-based threat analytics. Organizations are increasingly deploying solutions that assume nothing is trusted by default, constantly verify identity, monitor behavior, and automate responses to anomalous events.
Market Segments & Leading Solutions
Logical security in data centers is not monolithic; some solution areas are growing faster or commanding larger shares:
-
Identity & Access Management (IAM) leads early, accounting for roughly 35% of the solution share in 2025. This prominence reflects the fundamental importance of controlling who or what gets access, when, and under what conditions.
-
Other key solution types include Security Information and Event Management (SIEM), data encryption, vulnerability management, and others (e.g. threat intelligence, secure access gateways).
-
Deployment modes are split between cloud-based and on-premises solutions. While on-premises remains important for legacy systems and regulated industries, cloud-based offerings are growing faster due to scalability, lower capital cost, and ease of updates.
-
Organizational size matters: large enterprises currently account for about 70% of logical security demand. Their complexity, regulatory exposure, and resource capacity align nicely with comprehensive security investments. Small and medium-size enterprises (SMEs) are growing in uptake, but often constrained by cost, skills, or perceived risk.
Regional Highlights: United States, Europe & Asia-Pacific
-
United States is expected to lead in early adoption and growth. With strong regulatory pressure, large hyperscale and cloud data center deployments, and high cybersecurity spending, the U.S. market is likely to outperform many regions in 2025–2035 in terms of both value and innovation.
-
Europe will follow closely, driven by stringent privacy regulations, data protection laws, and demands for transparency and compliance. Countries like Germany, the U.K., and France are expected to be leaders within Europe for logical security spending.
-
Asia-Pacific is also a key opportunity zone. Rapid digital transformation, expanding cloud and data center infrastructure, rising investment in cybersecurity, and growing awareness among governments of data breach risks are all pushing demand upward. Although growth may start from a lower base relative to U.S./Europe, the forecast CAGR in Asia-Pacific is attractive.
Key Players & Competitive Landscape
The logical security market is populated by both long-standing cybersecurity incumbents and rapidly innovating challengers. Among the major names are:
-
IBM Corporation — with strength in identity and access management, enterprise security systems.
-
Cisco Systems — known for integrated networking plus security, including access control.
-
Check Point Software, Fortinet, Palo Alto Networks — also strong in threat prevention, firewalls, intrusion detection, and access management.
-
Symantec, McAfee, Trend Micro, CrowdStrike, FireEye — these companies contribute significantly, especially in vulnerability management, endpoint security, advanced threat detection, and incident response.
Competition is increasingly shaped by how well solutions integrate AI/ML, behavior-based analytics, zero-trust frameworks, ease of deployment across hybrid environments, and demonstrable compliance with regulation.
Request for Discount: https://www.factmr.com/connectus/sample?flag=S&rep_id=11155
Recent Developments & Innovation
-
The rising importance of zero-trust architectures has spurred companies to offer identity-centric access control, microsegmentation, and just-in-time privilege elevation.
-
AI and machine learning are being embedded in SIEM and threat detection platforms to improve anomaly detection, reduce false positives, and enhance automated response.
-
Increasing investment in multi-factor authentication and adaptive authentication methods, using biometrics, device posture, location and risk bandwidth to drive stronger IAM implementations.
-
Cloud service providers are bundling logical security features more tightly with their offerings, making it easier for customers to adopt secure models while shifting workloads to the cloud.
-
There’s also growing demand for encryption-at-rest and in-transit, particularly in privacy-sensitive industries like finance, healthcare, and government.
Challenges & Barriers
While momentum is strong, certain obstacles remain:
-
High upfront investment and complexity: Implementing comprehensive logical security (IAM, SIEM, encryption, etc.) often requires significant resources, both financial and technical. Integration with legacy systems can be especially difficult.
-
Skills shortage: Organizations sometimes lack enough qualified personnel to design, configure, maintain, and monitor logical security systems, especially in SMEs or in emerging markets.
-
Balancing security vs usability: Too much friction in access controls or authentication can degrade user experience and drive resistance; too little can leave gaps. Achieving the right balance is hard.
-
Regulatory variability: Different countries and sectors have different requirements for data protection, breach notification, identity verification, etc. Solutions need to be adaptable and compliant across jurisdictions.
-
Threat evolution: Attackers continually adapt. Security solutions must keep pace with evolving threat vectors, including supply chain attacks, identity theft, insider threat, and advanced persistent threats (APTs).
Buy Now at USD 2900: https://www.factmr.com/checkout/11155
Outlook & Strategic Recommendations
Looking ahead to 2035, the data center logical security market outlook is robust:
-
The market is expected to nearly triple, going from USD 12.8 billion in 2025 to approximately USD 38.5 billion by 2035.
-
Growth will be especially strong during the first half of that period (2025 to 2030), when value is expected to rise substantially as organizations accelerate security, often under regulatory pressure and driven by cloud migration.
-
Vendors who excel will likely be those who combine strong identity & access management, real-time threat intelligence, machine learning-based detection, native cloud/edge support, zero-trust features, and ease of deployment & integration.
For buyers (data center operators, enterprises, cloud providers), strategic priorities should include auditing logical security posture, adopting zero-trust where appropriate, ensuring encryption across both storage and transit, and choosing vendors whose solutions are compliant, scalable, and future-proof.